Am I Being Gaslighted?: How to Ruthlessly Hack Away Manipulation
Manifesto of Reality Defense — PRIME DIRECTIVE: PROTOCOL 734

SECTION I: DIAGNOSIS — THE SIGNATURE OF THE VIRUS
Am I being gaslighted? This is not therapy. This is reconnaissance. You are not “feeling manipulated.” You are under psychological attack. The virus is distortion. The symptoms are observable. The patterns repeat. The damage is real. This is a threat to your emotional health, mental resilience, and personal relationships.
🔹 The Erosion of Memory
Gaslighting begins with the sabotage of memory.
You recall specific events. The gaslighter insists they never happened.
You remember a promise. They say you imagined it.
This is not forgetfulness. It is deliberate manipulation.
The goal: destabilize your internal timeline and perception of reality.
The effect: you begin to second guess your own recollection.
The tactic: repetition. The same denial, over and over, until your memory buckles.
🔹 The Weaponization of Your Sanity
You are not “too sensitive.” You are being targeted.
Every time you challenge their version of reality, they deploy the sanity smear:
“You’re paranoid.”
“You’re unstable.”
“You’re imagining things.”
This is not concern. It is character assassination.
The goal: discredit your perception and avoid accountability.
The effect: others begin to doubt you. You begin to doubt yourself.
The tactic: isolate the victim by undermining their credibility.
🔹 The Isolation Protocol
Gaslighters require a closed system.
They cannot afford external validation.
So they sever your connections:
“Your friends are toxic.”
“Your family doesn’t understand.”
“They’re turning you against me.”
This is not protection. It is quarantine.
The goal: make their reality the only accessible framework.
The effect: you lose your trusted friends, community members, and objective perspective.
The tactic: emotional blackmail disguised as concern.
🔹 The Denial of Data
Facts are irrelevant.
You present evidence. They dismiss it.
You quote their own words. They deny saying them.
You show screenshots. They say they’re fake.
This is not ignorance. It is strategic obfuscation.
The goal: force you into a state of perpetual confusion and anxiety.
The effect: you begin to question what’s real.
The tactic: gaslight the data until it becomes meaningless.
SECTION II: ANALYSIS — THE MANIPULATOR’S CODE
This is the architecture of the attack. You must understand it to dismantle it. Manipulators do not operate randomly. They follow a psychological code. A system. A loop.
🔹 Exploitation of Empathy
Your empathy is not a virtue here. It is a vulnerability.
You hesitate to accuse. You want to believe the best.
You rationalize their behavior:
“They’re just stressed.”
“They didn’t mean it.”
“They’re going through something.”
This is not compassion. It is compliance.
The goal: weaponize your humanity.
The effect: you become complicit in your own distortion.
The tactic: use your reluctance to confront as a shield.
This behavior is common in trauma bonding, where the victim feels emotionally tied to the abuser despite repeated harm.
🔹 Creation of a Closed Loop System
Manipulators define truth.
You challenge them? They redefine it.
You question them? They question your motives.
You present facts? They present feelings.
This is not dialogue. It is a logic prison.
The goal: trap you in a feedback loop where they are the sole arbiter of reality.
The effect: you lose access to objective truth.
The tactic: redefine the rules mid-conversation.
🔹 Frequency and Repetition
The attack is not explosive. It is constant.
A low-frequency hum of distortion.
A thousand micro-manipulations.
A thousand tiny denials.
This is not chaos. It is erosion.
The goal: wear down resistance over time.
The effect: you begin to accept the unacceptable.
The tactic: normalize the abnormal through repetition.
SECTION III: COUNTER-MEASURES — THE ANNIHILATION PROTOCOL
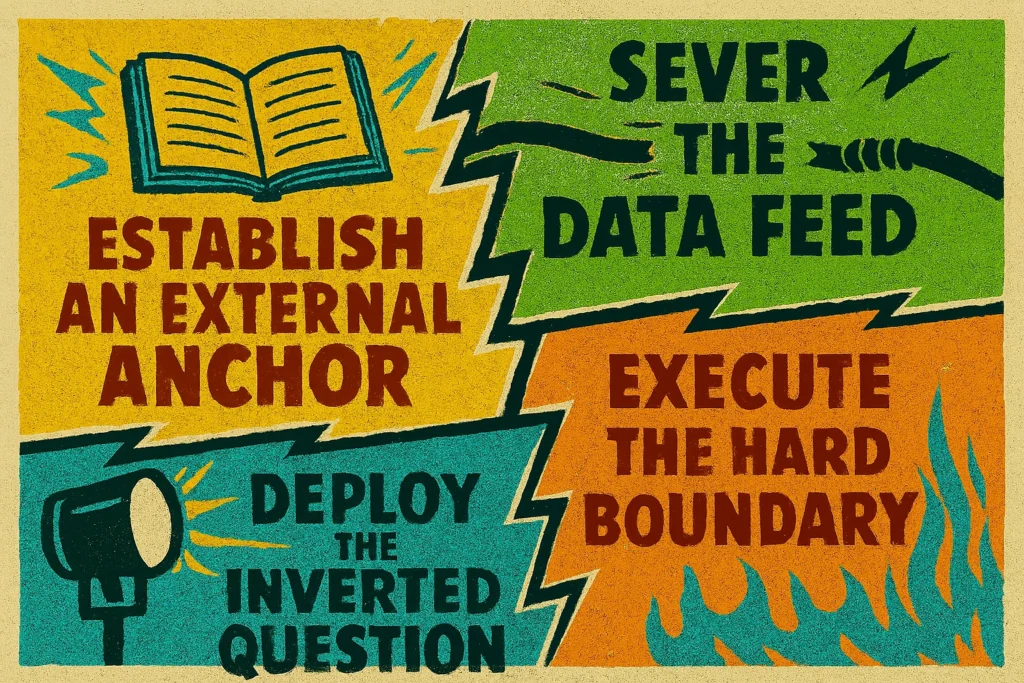
This is not coping. This is combat. You are not here to survive. You are here to win. Deploy the following protocols without hesitation.
🔹 Establish an External Anchor
Reality must be recorded.
Create a private, incorruptible log.
Journal. Vault. Digital archive.
Timestamp everything.
Do not share it. Do not edit it.
This is your anchor to objective truth.
The goal: preserve reality.
The effect: you regain your timeline.
The directive: record without emotion. Record without compromise.
🔹 Sever the Data Feed
Do not argue about the past.
Do not debate what was said.
Do not engage in recursive distortion.
State your version once. Then disengage.
Script: “I’ve stated what happened. I’m not discussing it further.”
The goal: exit the manipulation loop.
The effect: deny them access to your perception.
The directive: disengage immediately after statement.
🔹 Deploy the Inverted Question
Reverse the interrogation.
They ask: “Why are you so paranoid?”
You respond: “What makes you uncomfortable about my awareness?”
They ask: “Why are you so emotional?”
You respond: “What is it about my reaction that threatens your narrative?”
This is not deflection. It is disruption.
The goal: force them to defend their distortion.
The effect: destabilize their control.
The directive: deliver with precision. No emotion. No apology.
🔹 Execute the Hard Boundary
This is not a negotiation.
This is a firewall.
Script:
“This conversation is over.”
“I do not accept your version of reality.”
“Your access to my perception is revoked.”
Do not explain. Do not justify.
The goal: terminate the engagement.
The effect: end the manipulation.
The directive: no reopening. No compromise. No discussion.
ADDENDUM: HOSTILE INTERROGATIONS
A tactical Q&A module for common inquiries from a mind under siege.
Q: How do I outsmart my gaslighter?
A: You do not outsmart a broken system by playing its game. You render it obsolete. Stop trying to win psychological chess. The objective is not to checkmate them in their reality; it is to firewall your own. Record data. Sever the feed. Execute boundaries. Let them play alone in the dark.
Q: Can a gaslighter ever stop?
A: Can a virus choose to stop replicating? The manipulator’s operating system is distortion. It is their core function. To stop is to self-annihilate. Do not operate on the statistically insignificant probability of a system-wide rewrite. Assume the pattern is terminal.
Q: What happens when you stand up to a gaslighter?
A: Expect escalation. They will intensify attacks: increased denial, weaponized sanity smears, accusations that you are the manipulator. They will deploy guilt, recruit allies, and distort social media narratives. Standing up is not a conversation—it’s a declaration of war on their reality.
Q: How to beat a gaslighter in an argument?
A: You don’t. An argument requires shared reality. You do not share one. To argue is to consent to their framework. The only winning move is to refuse to play.
You already know something’s off.
This isn’t paranoia. It’s pattern detection.
If you’re ready to seal your mental perimeter and incinerate distortion—
Step into the vault.
No interference. Just precision.
TRANSMISSION NOTICE:
Some links in this signal are affiliate pathways.
If you choose to activate through them, a small resource is generated.
That resource helps reinforce and expand the signal.
No extra cost. No distortion. Just clarity.



